The Pyramid of Pain is a framework that helps security teams prioritize their efforts by identifying the most valuable indicators of compromise (IOCs) that are most likely to lead to the detection and prevention of cyber threats. In this blog post, we’ll explore what the Pyramid of Pain is, how it works, and how MSSP can help operationalize for better defense.
What is the Pyramid of Pain?
The Pyramid of Pain is a framework developed by David J. Bianco to help security teams prioritize and understand the value of different types of IOCs. The pyramid illustrates the relative difficulty and value of different types of IOCs to attackers and defenders, with the most valuable IOCs at the top of the pyramid and the least valuable at the bottom.
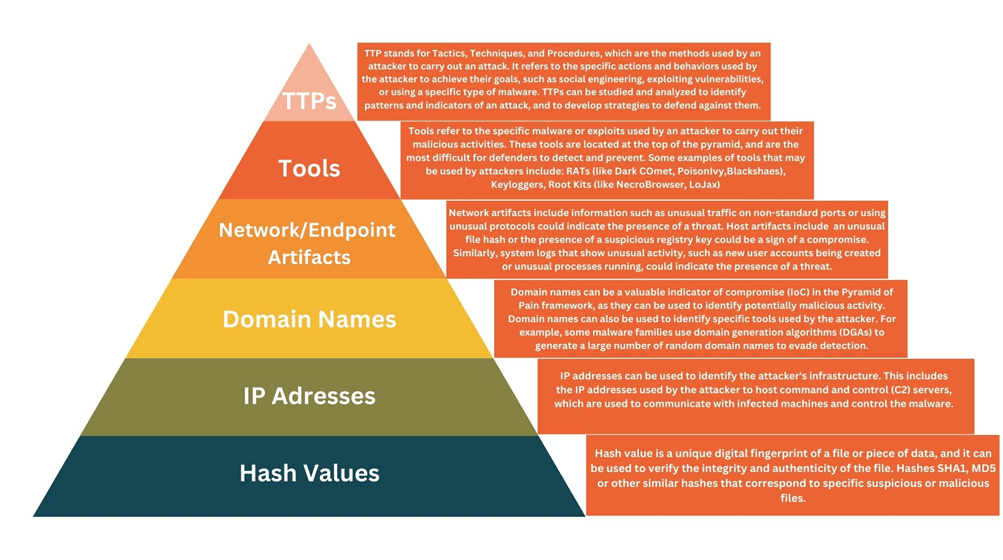
Below are The Four pillar of the Pyramid of Pain
Level 1: Indicators of Compromise (IOCs)
IOCs are the most basic level of the Pyramid of Pain. These are typically pieces of information that indicate a potential threat, such as an IP address, domain name, or file hash. IOCs are relatively easy to obtain and can be used to identify known malicious activity. However, they are also easy for attackers to change, making them less useful over time.
Level 2: Tactics, Techniques, and Procedures (TTPs)
TTPs are the second level of the Pyramid of Pain. These are more valuable than IOCs because they provide information on how an attacker operates, rather than just what they are using to execute the attack. TTPs can include details on how an attacker gains access to a system, how they move laterally within a network, or how they exfiltrate data. TTPs are more difficult to obtain than IOCs but are also more valuable because they can help identify unknown threats.
Level 3: Campaigns
Campaigns are the third level of the Pyramid of Pain. These are long-term, multi-stage attacks that are carried out by advanced persistent threat (APT) groups. Campaigns can last for months or even years, and they involve multiple tactics and techniques. By tracking the entire lifecycle of a campaign, security teams can gain a deeper understanding of how an attacker operates and can develop more effective defense.
Level 4: Strategic Intelligence
Strategic intelligence is the most valuable level of the Pyramid of Pain. This involves understanding the motivations and goals of an attacker, as well as their resources and capabilities. Strategic intelligence is more difficult to obtain than the other levels, but it can provide the most significant insights into the threat landscape. By understanding the strategic goals of an attacker, security teams can develop proactive defense that are better able to prevent future attacks.
How SOC365 can help?
SOC365 as Managed Security Service Provider (MSSP) in Dubai, UAE can help organizations implement the Pyramid of Pain framework in several ways. Here are a few examples:
Threat Intelligence Gathering: SOC365 can provide valuable threat intelligence gathering services, which involve collecting and analysing information on emerging threats, attack patterns, and malicious actors. This can help organizations identify the most valuable IOCs and prioritize their defensive efforts accordingly.
Security Information and Event Management (SIEM): SOC365 can help organizations implement and manage SIEM solutions, which can automatically collect, correlate, and analyse security event data from multiple sources. This can help organizations detect and respond to potential security incidents more quickly and effectively.
Threat Hunting: As a leading Cyber Threat Hunting Services in Dubai, UAE SOC365 can perform proactive threat hunting activities to identify hidden threats within an organization’s network or infrastructure. This can involve analysing logs, network traffic, and other data sources to uncover malicious activity and identify the most valuable IOCs.
Security Operations Centre (SOC) Services: SOC365 can provide SOC services, which involve monitoring an organization’s network and infrastructure for potential threats, and responding to security incidents in real-time. This can help organizations identify and respond to the most valuable IOCs more quickly and effectively.
Incident Response Planning: As the best Incident Response & Malware Analysis Services in Dubai, UAE SOC365 can help organizations develop and implement incident response plans, which outline the procedures and protocols to follow in the event of a security incident. This can include guidelines for prioritizing and responding to different types of IOCs, based on their relative value and difficulty.
By leveraging the expertise and resources of a leading MSSP, organizations can more effectively implement the Pyramid of Pain framework and prioritize their defensive efforts based on the most valuable IOCs. This can help organizations reduce their risk of cyber-attacks and minimize the impact of any security incidents.

