What is Threat Hunting?
Threat hunting is a proactive approach to cybersecurity that involves actively searching for threats and vulnerabilities in an organization’s IT environment. While there are many different strategies and techniques that can be used for threat hunting, one important aspect is the creation of a hypothesis playbook.
A hypothesis playbook is a document that outlines potential threats and vulnerabilities in an organization’s IT environment, along with the indicators of compromise (IOCs) and other evidence that may be associated with those threats. By creating a hypothesis playbook, threat hunters can more effectively identify and investigate potential threats, and respond more quickly and effectively to any security incidents that occur.
Here’s an example of how to create a hypothesis playbook for a hypothetical organization:
– Identify the assets and data that are most critical to the organization. This may include customer data, intellectual property, or other sensitive information.
– Review the organization’s security policies and compliance requirements to identify any areas of potential risk. This may include compliance violations, unsecured endpoints, or weak passwords.
– Review the organization’s IT infrastructure, including the network, servers, and applications, to identify any vulnerabilities or areas of weakness.
– Identify any recent security incidents or threats that may be relevant to the organization. This may include news of a new malware variant, a vulnerability in a commonly used application, or a recent data breach at a similar organization.
– Develop a hypothesis for each potential threat or vulnerability. This should include the IOCs and other evidence that may be associated with the threat, such as unusual network traffic or suspicious log entries.
Let us understand the phases involved in the creation of the Hunt Hypothesis.
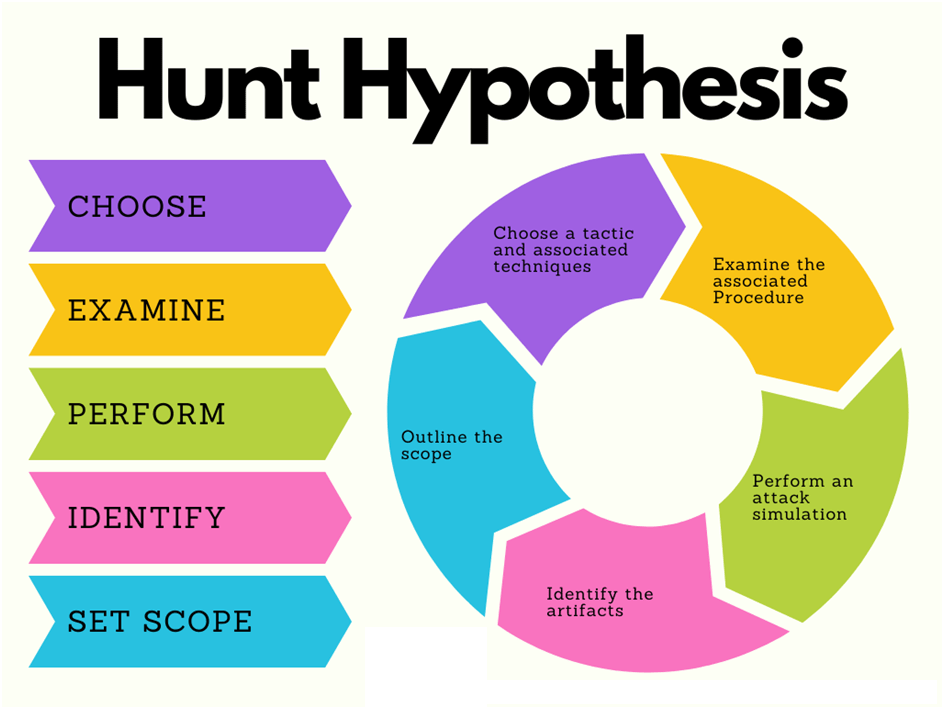
Choose a tactic and associated technique:
Tactics represent the “why” of an ATT&CK technique or sub-technique. It is the adversary’s tactical goal: the reason for performing an action. For example, an adversary may want to achieve credential access. Identify a tactic and associated technique using MITRE Framework that may pose a threat to your organization. Understand various sub-techniques and procedures used by an adversary to accomplish the attack goal.
Examine the associated procedure:
Procedures are the specific implementation the adversary uses for techniques or sub-techniques. For example, a procedure could be an adversary using DNS application layer protocol to exfiltrate the data to attacker C2 server. It is crucial to understand the procedure used under a given technique/sub-technique which is helpful in developing a hypothesis for the hunt.
Attack Simulation:
Attack simulation is the practice of simulating cyberattacks based on the observed procedures of a given technique/sub-technique. This can help enhance threat-hunting capabilities by providing a more realistic understanding of how attackers operate in the real world. By threat simulation, Hunters can identify behavior related to new indicators of compromise (IOCs) and artifacts to build effective detection.
Identify the artifacts:
This phase involves understanding the behavior of the simulated attack by analyzing and collecting the required evidence from network and endpoint logs. For example, abnormal network connections, Suspicious PowerShell execution/suspicious registry, and system file changes.
Hunting Scope:
The motive of this phase is to define the hunting scope after gathering the required information. The scope would cover:
– Data source required to start your hunt (For Instance: Sysmon, NIDS).
– Hunting duration and frequency.
Let’s look at a Real-world scenario for creating threat hunting hypothesis,
Tactic: Command and control
Technique: Application Layer Protocol: DNS (Sub-technique of: T1071)
Procedure: Adversaries may communicate using the Domain Name System (DNS) application layer protocol to avoid detection/network filtering by blending in with existing traffic. Often known as DNS tunneling, adversaries may abuse DNS to communicate with systems under their control within a victim network while also mimicking normal, expected traffic.
Data sources:
Required Data sources for detecting DNS tunneling are DNS server logs, DNS query logs, and DNS traffic analysis tools.
Tools: ELK, CrowdStrike
Hypothesis:
Below is a sample hypothesis based on certain common behavior. However, should not be limited to:
– Adversaries may use DNS protocol for beaconing using DGA to evade detection to their command-and-control server to get instructions from command-and-control systems. Therefore, analyzing for excessive NXDomain responses within a short period of time could potentially detect an infected system.
– Creating a hypothesis to examine for any uncommon DNS record type may also be helpful in detecting DNS tunnels. For Example, analyzing any DNS query that returns a TXT record containing a string of characters that are not commonly used in legitimate TXT records (i.e., base64 encoded data, unusual character sets).
Response:
– Identify the beaconing activity and quarantined the infected system to clean, Initiate malware scan to detect any malware infection.
– Implement DNS sinkhole feature to block the suspicious DNS queries and responses used by the attackers.
– Adapt Defense in depth security strategy by implementing analysis rules using payload and Traffic.
– Alert the appropriate incident response team members and stakeholders, such as network administrators, security analysts, or management.
– Conduct a thorough review of the organization’s DNS configurations to identify potential weaknesses or gaps that could be exploited by attackers.
– Implement DNS security controls, such as DNSSEC and DNS filtering, to prevent beaconing activity in DNS traffic.
As a leading Cyber Threat Hunting service in Dubai, SOC 365 with skilled hunters can help operationalize threat hunting and create IR playbooks to effectively identify and respond to security incidents, reducing the risk of data breaches and other cybersecurity threats.

