Zero Trust Architecture (ZTA) has been gaining popularity as a cybersecurity framework for modern organizations. ZTA is a security model that focuses on maintaining strict access control and limiting user privileges, instead of relying solely on perimeter-based security measures. In this blog, we will discuss the requirements, use cases, and advantages of ZTA, as well as how Managed Security Service Providers (MSSPs) provide Zero Trust Network Access (ZTNA) services to clients.
Foundation of Zero Trust architecture
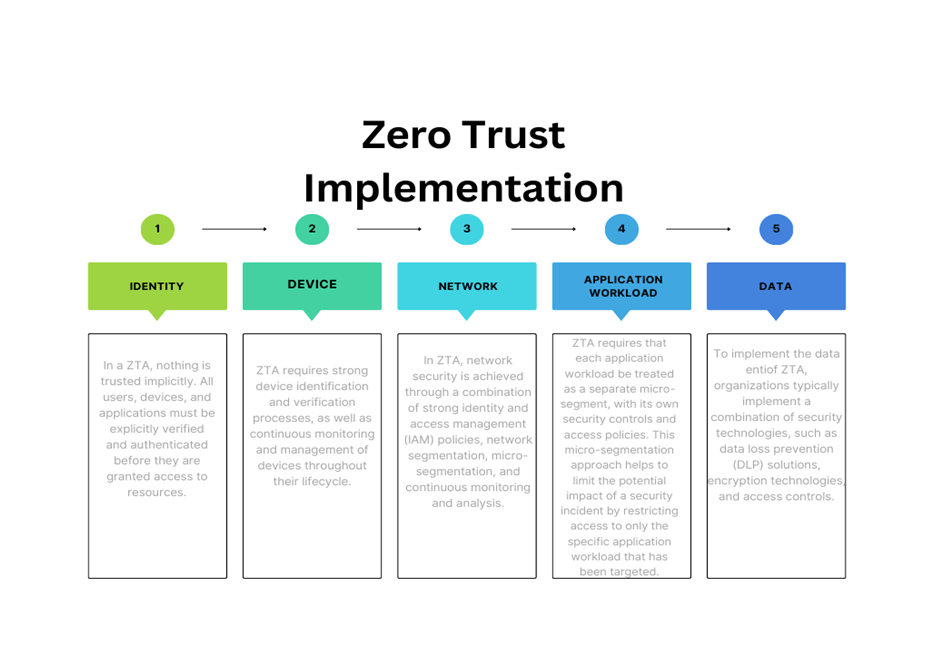
Requirements of ZTA
ZTA requires an organization to adopt a set of security principles and technologies to reduce the risk of data breaches and cyber-attacks. The key requirements for ZTA are as follows:
– Identity verification: ZTA requires all users, devices, and applications to be authenticated and authorized before accessing any resources or data.
– Least privilege access: ZTA ensures that users are only granted access to the resources they need to do their jobs, and nothing more.
– Segmentation: ZTA requires the segmentation of network resources into smaller zones to reduce the impact of a potential security breach.
– Visibility and monitoring: ZTA require the implementation of a comprehensive monitoring and logging system to detect and respond to any unusual activity.
– Micro-segmentation: ZTA requires the implementation of micro-segmentation to enforce granular access controls on a per-application or per-workload basis.
Use Cases of ZTA
ZTA can be implemented in various use cases, such as:
– Remote workers: With the increase in remote workforces, ZTA is an ideal solution for securing remote access to critical applications and data.
– Multi-cloud environments: ZTA can help organizations secure multi-cloud environments by providing a unified security framework that can be applied across all cloud services.
– Compliance requirements: ZTA can help organizations meet compliance requirements by providing strong access controls and a comprehensive auditing and monitoring system.
– Legacy systems: ZTA can be used to secure legacy systems by implementing secure access controls and segmentation.
Advantages of ZTA
The key advantages of ZTA are as follows:
– Improved security posture: ZTA helps organizations reduce the risk of data breaches and cyber-attacks by providing granular access controls, micro-segmentation, and strong authentication and authorization protocols.
– Increased productivity: ZTA can increase productivity by providing secure access to resources from anywhere, at any time, and from any device.
– Simplified security management: ZTA provides a unified security framework that simplifies security management across multiple environments.
– Reduced costs: ZTA can help organizations reduce costs by eliminating the need for traditional perimeter-based security measures.
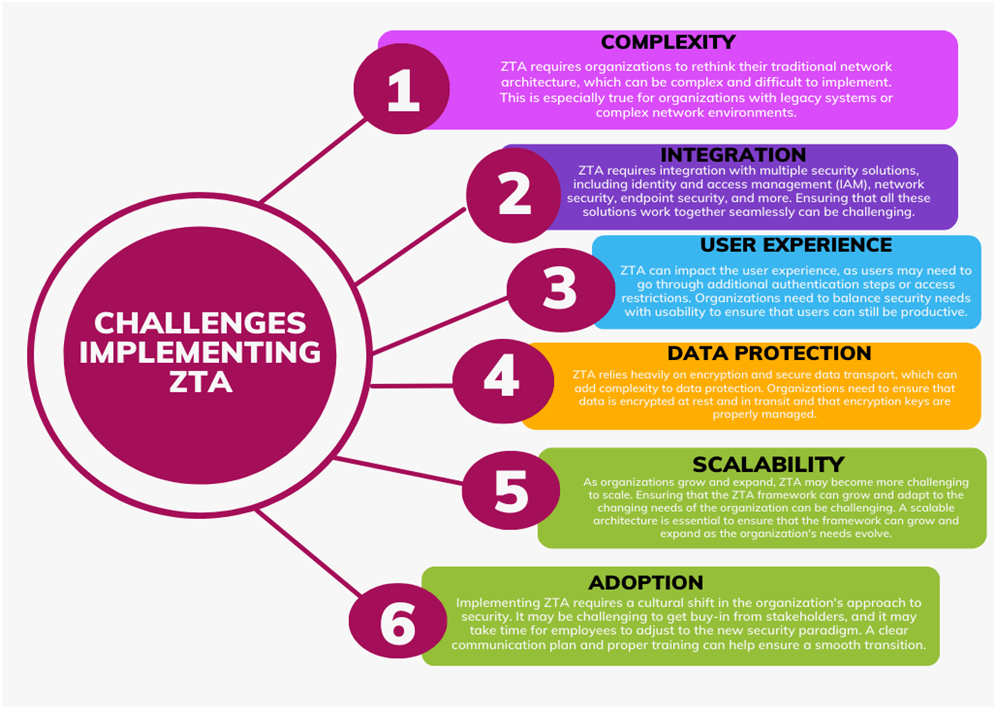
Challenges
While ZTA has many benefits, it also presents several challenges that organizations must overcome to successfully implement it.
MSSP ZTNA Service to Clients
MSSPs provide ZTNA services to clients by leveraging various security technologies such as Identity and Access Management (IAM), network segmentation, and encryption. Here are some of the ways MSSPs provide ZTNA services to clients:
– IAM solutions: MSSPs provide IAM solutions that enforce strict access control policies, multi-factor authentication, and user identity verification.
– Micro-segmentation: MSSPs implement micro-segmentation to create smaller network zones that enforce granular access controls based on a user’s role and privilege level.
– Encryption: Managed security service providers implement encryption to secure data in transit and at rest, ensuring that sensitive data is protected from unauthorized access.
– Network monitoring and detection: MSSPs provide 24/7 network monitoring and cyber incident response service to detect and respond to any unusual activity, reducing the risk of data breaches and Ransomware attacks.
In conclusion, ZTA is an effective cybersecurity framework that helps organizations reduce the risk of data breaches and cyber-attacks by enforcing strict access control and limiting user privileges. MSSPs provide ZTNA services to clients by leveraging various security technologies, such IAM, Network security, Endpoint security, Cloud security, by combining these and other security technologies, MSSPs can provide ZTNA services that offer robust protection against ransomware attacks.
As the leading Cyber Security Consultant in Dubai, UAE, in order to handle threats to a company’s computer networks and computer systems, it is our responsibility to discover issues, analyse security concerns, determine risk, and implement solutions. In order to establish the best strategy to protect a company’s data, we examine every level of the computer systems within the organisation and how those systems relate to one another.

